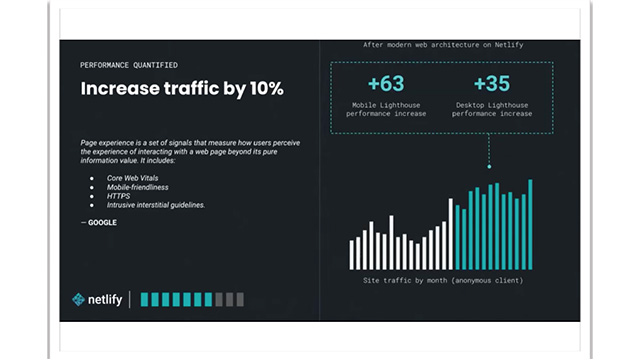
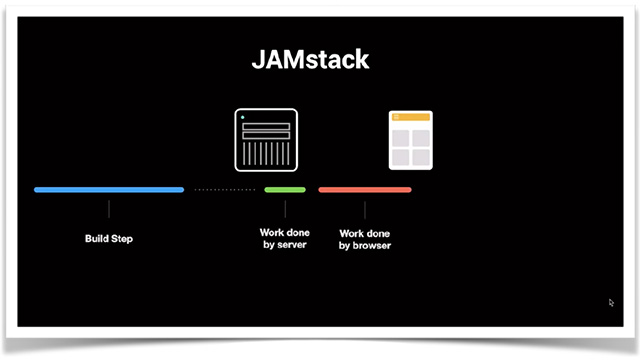
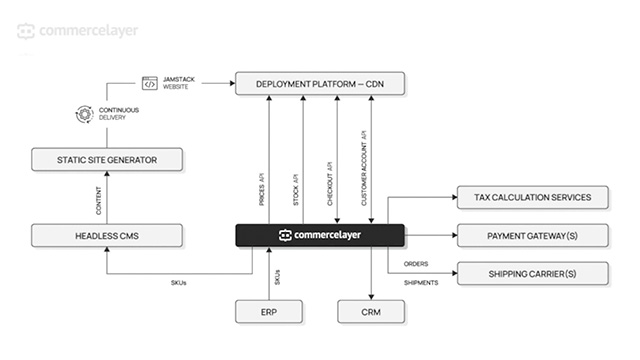
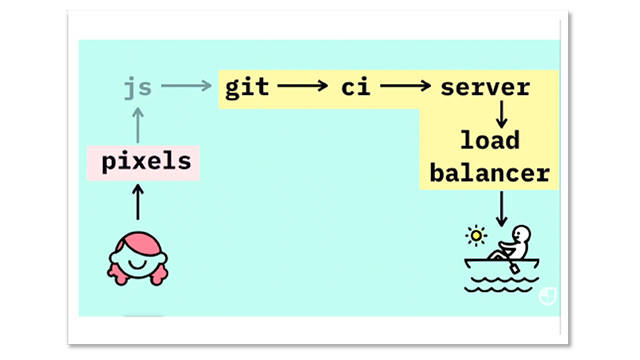
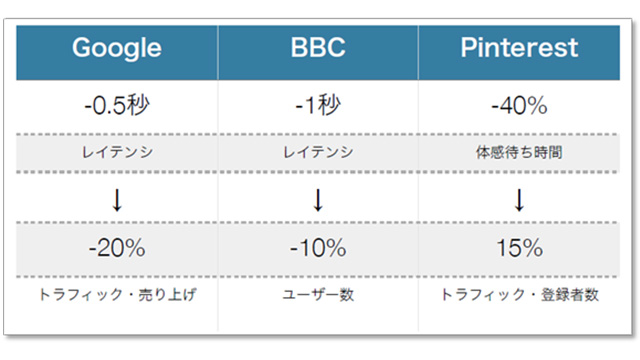
This time, we will introduce the content of the presentation titled "Security is the 's' in Jamstack" from the "Jamstack Conference 2021"!
The "Jamstack Conference," which has over 10 years of history, is hosted by Netlify, the cloud computing company that created Jamstack. Developers from around the world gather to discuss the design and development of the latest websites based on the Jamstack concept. The presentations are in English, but this blog will introduce them in Japanese.
- Table of Contents
-
- Security-related Issues
- Types of Authentication Methods
- 1. Centralized Authentication
- 2. Decentralized Authentication
- Four Approaches
- Approach 1: Create a Centralized Authentication System
- Approach 2: Create a Custom Decentralized Authentication
- Approach 3: Outsourcing Centralized Authentication
- Approach 4 Outsourcing Decentralized Authentication
- Comparison of Approaches
- Summary
The speaker this time is engineer Maricris Bonzo from a company called Magic.
We provide decentralized authentication services.
How can we ensure security in Jamstack?
They introduced four approaches for personal authentication.
Security-related Issues
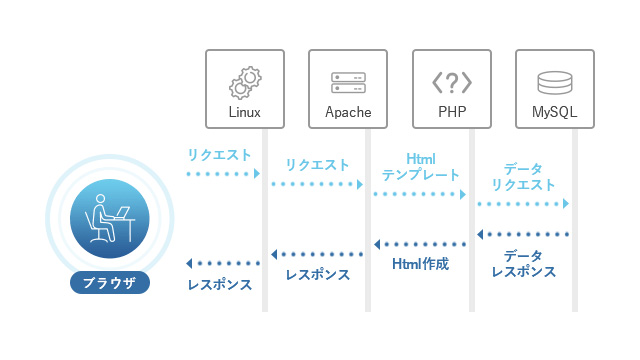
It is common for users to log in and register personal information when using the system.
However, at the same time, you will face the following risks.
Service Provider
As the scale expands, the need and pressure to manage data properly increases.
[User Side]
How personal information is managed, concerns about data leakage. (I wonder how my data will be managed...)
How can we address this issue when using Jamstack?
Types of Authentication Methods
As a fundamental premise, there are two main types of authentication methods.
1. Centralized Authentication
Conventional authentication methods. It aggregates and manages users' personal information data.
It seems that terms such as centralized authentication, aggregated authentication, centralized authentication, and central authority authentication can be used in Japanese, but there is no fixed expression established.
This report will refer to it as "centralized authentication."
2. Decentralized Authentication
New authentication method. Each user manages their own personal data.
The term "decentralized authentication" is often used.
Four Approaches
This is the main topic.
Approach 1: Create a Centralized Authentication System

There are ways to use IDs and passwords, or to issue tokens.
The system has the advantage of being easy to create and customizable to suit various applications for managing data.
On the other hand, we cannot overlook the risks from the perspective of data management. Even when using libraries, it is extremely difficult to find reliable open source options.
Approach 2: Create a Custom Decentralized Authentication

To mitigate the risks of managing data in-house, the concept of decentralized authentication has emerged. Instead of the system managing data centrally, each user manages their own data.
Keep keys and certificates on your mobile phone and distribute them on the blockchain, presenting only the necessary data as needed.
However, creating it yourself can be quite challenging, and ensuring its reliability may also be difficult.
Approach 3: Outsourcing Centralized Authentication

This is a common method used today, which relies on authentication through other services using APIs.
This includes multi-factor authentication (MFA) and single sign-on (SSO).
This is an easy way to create sites with Jamstack.
The services provided by Auth0 and Firebase have high compatibility. The ability to quickly integrate them just by learning how to use the APIs of these providers is a major attraction.
However, regardless of which centralized authentication service is used, there is certainly a risk in having the data managed in a centralized manner. If that service goes down, it becomes unusable. Additionally, the number of people who feel resistance to not being able to manage their own data is likely to increase in the future.
Approach 4 Outsourcing Decentralized Authentication
In decentralized authentication services, instead of a user ID and password, a private key and public key managed by blockchain are provided.
The company Magic, where the speaker works, is a specialized service provider.
Those private and public keys are, so to speak, like a physical strengthening of traditional user IDs and passwords.
These keys generated by elliptic curve cryptography do not contain any personally identifiable information.
Therefore, it is also possible to migrate to and use other services.
The usage varies by service provider. Magic offers an API that can be used with plug-and-play (implementation is very easy!).
User information and data belong to the user. It can be said that this aligns with the thinking that will become a future trend.
However, being in a growth phase in a new field is both an advantage and a disadvantage.
There are still no established standards, and it varies widely among providers.
Additionally, you may feel that there are some limitations on what can be done since the authentication will be outsourced.
Comparison of Approaches
We have compared the four approaches introduced so far.
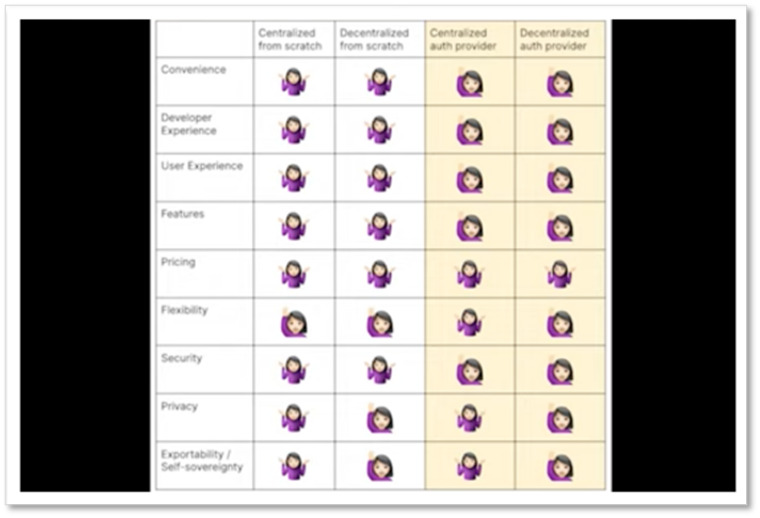
The result is that the third or fourth outsourcing approach is superior.
In addition, the points to consider were introduced as follows.
1. Ease of Developer Engagement
2. User Experience
3. Features Provided
4. Level of Support
5. Current and Future Costs
6. Stringency of Privacy and Security
7. Can users have sovereignty over their data?
Summary
The concept of decentralized authentication seems to be gradually gaining traction.
Microsoft
(https://www.microsoft.com/en-us/security/business/solutions/decentralized-identity)
NTT Data
Recently, there has been a trend towards extreme tightening in the way personal information is managed.
Regulations such as the EU General Data Protection Regulation (GDPR) have become very strict, making it so that Yahoo Japan may no longer be accessible from Europe, and even Facebook may become unusable, among other things...
From this, there are advantages to a method of managing personal data that is decentralized and not involving others, as opposed to a method that aggregates personal information.
Additionally, obtaining authentication via API aligns with the design philosophy of Jamstack, and it can be said to be a good approach as it does not impose unnecessary responsibilities.
However, the reality is that there are few experienced individuals who have actually implemented it, making it difficult to find talent.
That is why touching on such methods early on may become a significant advantage in the future!
Thank you for reading until the end.
Human Science Co., Ltd. provides solutions for web content and platforms using a unique combination of "document production know-how" and "the latest web development technology (Jamstack)" that is not available from other companies.
If you are interested, please feel free to contact us here!
Human Science Co., Ltd.
https://www.science.co.jp/document/jamstack.html
Source of this document: https://www.youtube.com/watch?v=FFQctR6w11M