Company
Information management/quality management
INFORMATION MANAGEMENT
Information management
Mechanism for information management
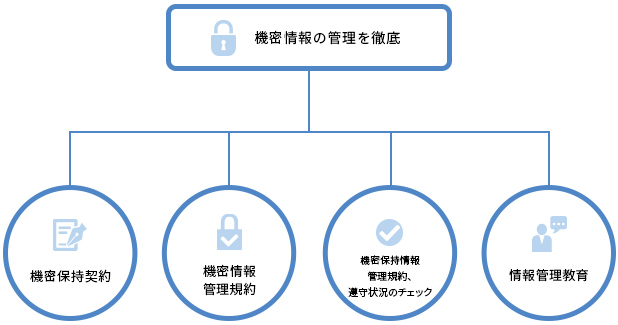
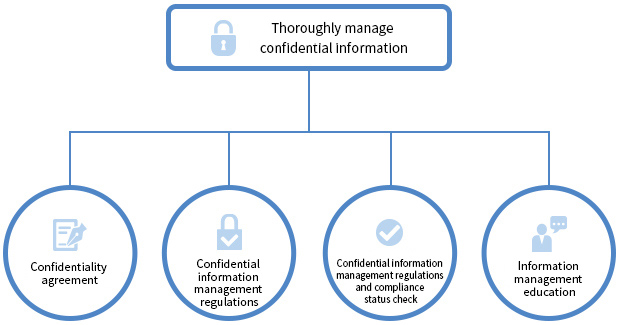
Human Science operates a system to manage customers' important confidential information.
The company and its employees have signed a confidentiality agreement. We have established confidential information management regulations as a policy for information management. Every year, we check the compliance status of employees with confidential information management regulations. Additionally, we provide information management training to our employees every year.
We also have confidentiality agreements with our collaborating staff.
Control of entry and exit to office space
Entry and exit to the office floor is managed using IC cards held only by employees.

Use of security room
There are times when it is necessary to create a manual for a product before its release, in an environment where it is not visible to other people. There is a security room, and only those involved in the project can enter and work there. The facility is managed using a PIN code set by the person concerned to prevent unauthorized persons from entering and exiting.


International standard JIS Q 27001:2014 (ISO/IEC 27001:2013) certification for ISMS (Information Security Management System)
Human Science Co., Ltd. has obtained the international standard "JIS Q 27001:2014 (ISO/IEC 27001:2013)" certification for ISMS (Information Security Management System) and is currently maintaining and operating it.

First registration date: June 18, 2012
Certification standard: JIS Q 27001:2014 (ISO/IEC 27001:2013)
Certification registration number: JP12/080233
Certification registration body (certification number): SGS Japan Co., Ltd. Certification/Business Solution Service (ISR021)
Registration range:
1. E-learning production, implementation and operational support
2. Translation
3. Document/manual creation
4. Collection and creation of AI learning data
ISMS basic policy
Date of Establishment: December 9, 2010
Date of Revision: October 24, 2023
Representative Director: Tsuyoshi Kumazawa
Human Science Co., Ltd.'s corporate philosophy (value of existence) is ''Human Science supports domestic and overseas companies with technology centered on technical communication and IT, and contributes to the realization of a prosperous and dream-filled society.'' We operate our business under the corporate philosophy, and support the operations of many companies and various organizations. When doing so, we collect a lot of information from you. We also handle a lot of information about our employees and other related parties. We position the protection of information assets as an important issue in conducting business while maintaining relationships of trust with customers and related parties. It is important to safely protect information assets entrusted to us by customers and related parties to prevent accidents such as loss, theft, or unauthorized use. Therefore, we will implement physical and technical security measures. It is also important that employees have a high level of awareness about information security and strive to protect information assets.
Therefore, we have hereby established our "ISMS Basic Policy" as a guideline for appropriately protecting the information assets held by our company, and we will implement the Information Security Management System (ISMS) in accordance with this basic policy. All employees, including management, fully understand the purpose of this basic policy and act in compliance with internal rules regarding our information security management system.
1. Definition of information security
At our company, information security is defined as maintaining the confidentiality, integrity, and availability of information assets.
2. Scope of Application
Our company practices ISMS activities within the following scope.
Target Business/Operations: E-Learning Business, Document Solutions Business, Localization Business, Annotation Business, Administration Business, Sales Business
Target Departments: All departments (excluding CS Promotion Department and Offshore Development Department)
Target Office: Human Science Co., Ltd. Headquarters
3. Manager's Responsibilities
The Company appoints an information security manager who is responsible for information security. The information security manager is responsible for implementing measures to protect the Company's information assets and taking prompt action when an event that threatens information security is discovered.
4. Employee Responsibilities
Our company provides education to all employees, including temporary employees, so that everyone understands the "ISMS Basic Policy" and internal rules related to ISMS, and acts with the belief that it is their responsibility to act in compliance with the rules.
5. Identifying information assets and taking countermeasures
We identify information assets that should be protected, such as confidential information and personal information. In order to protect the identified information assets, we regularly analyze and evaluate risks and take optimal protection measures according to the risks.
6. Personal information protection
Our company will handle personal information in compliance with applicable laws, regulations, etc. regarding the personal information we handle.
7. Legal compliance
Our company promotes activities to appropriately comply with laws and concluded contracts related to information security.
8. Promotion of information security management
Our company conducts activities to maintain information security led by the information security manager, confirms that information security is maintained through audits and management reviews, and promotes continuous improvement activities for constant correction and prevention.
9. Business continuity
We will take the necessary measures to appropriately continue our important business.
Privacy policy
Revision date: October 30, 2023
Representative Director Tsuyoshi Kumazawa
Introduction
Human Science Co., Ltd. (hereinafter referred to as the ''Company'') protects information that can specify and identify individuals (hereinafter referred to as ''Personal Information''), such as an individual's name, address, telephone number, email address, and career history, in compliance with laws and regulations and other norms related to the handling of personal information. In addition, we have established the following personal information protection policy and will continue to review and improve it in order to handle personal information assets appropriately.
Article 1 Regarding acquisition of personal information
Our company will acquire personal information legitimately without using false or other illegal means.
Article 2 Regarding use of personal information
Our company will use personal information within the scope necessary to achieve the following purposes of use.
When using personal information for purposes not specified below, we will do so after obtaining the consent of the individual in advance.
・Responses to requests for quotation/consultations and sending of materials
・Providing information about seminars and various services
・Selection of applicants for employment and notification of results
・Providing, improving and developing our products (including updates, troubleshooting, and support)
・Administrative affairs/tax procedures related to transactions, , and related operations
・Distribution of behavioral targeting advertisements on specific sites using programs provided by advertisement distribution companies
・Analysis of attribute information, behavior history, etc. acquired by our company in order to understand users' hobbies, preferences, etc.
Article 3 Regarding the security management of personal information
Our company will take necessary and appropriate measures to prevent the leakage, loss, or damage of personal information it handles, and to manage the safety of personal information.
Article 4 Regarding entrustment of personal information
When entrusting all or part of the handling of personal information to a third party, our company conducts a strict investigation and selection of the third party, and provides necessary and appropriate supervision over the third party to ensure the safe management of the personal information entrusted with the handling of the third party.
Article 5 Handling of personal information regarding jointly sponsored seminars
For seminars where we have specified a third party (hereinafter referred to as a "co-sponsor") with whom we are co-hosting the seminar, we may use all or part of your personal information jointly only with that co-sponsor. Personal information provided will be handled appropriately based on our "Privacy Policy".
・Scope of personal information to be jointly used
Information entered in the application form, such as name, affiliation, email address, etc.
Responses to the seminar questionnaire
・Scope of joint users
Our company and co-sponsors
・Purpose of joint use
Identity confirmation at the time of seminar registration
Seminar information/inquiry response
Announcement of events, product information, etc. provided by our company and co-sponsors
Seminar improvements
・Name of the person responsible for the management of personal data to be jointly used
Human Science Co., Ltd., Document Solution Department, Consulting Group
・How to obtain personal information
Seminar application form, seminar questionnaire (web)
Article 6 Security measures and use of cookies
Our website uses cookies to improve user experience and collect browsing history information, etc.
Cookies are a function by which a web server temporarily writes and stores data on a user's computer. It does not contain any information that can personally identify users, and will not have any negative impact on your computer.
Article 7 Regarding provision of personal information to third parties
Our company will not provide personal information to third parties without obtaining the consent of the person in advance, except as stipulated by laws and regulations such as the Personal Information Protection Act.
Article 8 Disclosure, correction, etc. of personal information
If a person requests disclosure of his/her personal information, our company will promptly disclose it.
If we cannot confirm your identity, we will not accommodate the request to disclosure. If there is an error in the content of personal information and the person requests correction, addition, deletion, suspension of use, etc., we will investigate and respond promptly. If we cannot confirm your identity, we will not accommodate these requests.
If you have any requests or inquiries regarding our handling of personal information, please contact us below.
[Contact information]
Human Science Co., Ltd.
Personal information inquiry desk
E-mail: privacy@science.co.jp
Phone: +81-3-5321-3111
About anonymously processed information
Our company acquires, uses, manages and provides anonymously processed information in compliance with laws, regulations, etc.
Items for using anonymously processed information
Still image information inside the body (intraperitoneal cavity) obtained during a surgical operation (External information such as the doctor's and patient's faces is not included. Still image metadata does not include any description that can identify a specific individual. )
How to provide anonymously processed information
We provide information on servers or cloud servers that have advanced security measures in place to prevent information leaks, theft, etc.
Quality ManagementQUARITY MANAGEMENT
ISO9001 quality policy
Date of Establishment: August 1, 2022
Representative Director Tsuyoshi Kumazawa
1. Basic Philosophy
We, at the Technical Communication Group, based on our corporate philosophy of "supporting domestic and international companies with technical communication and IT, and contributing to the realization of a rich and dream-filled society," will work together, discuss, and execute to achieve this goal, always striving for stable and improved quality.
2. Quality Policy
(1) We will set quality objectives and carry out activities to achieve this quality policy.
(2) We aim to improve customer satisfaction and continuously improve compliance with requirements and the effectiveness of the quality management system.
(3) All employees are aware of their roles and responsibilities in quality management and will work together to execute them.
(4) This quality policy will be made public to external parties through our corporate website.
International standard for quality management systems ISO 9001:2015 certification
Human Science Co., Ltd. has obtained certification for the international standard "ISO 9001:2015" for quality management systems. We will continue to strive for stable and improved quality in order to provide satisfactory services to our customers.

Language Solutions Department
Multi-lingual Translation Group
Certification acquired at the Localization Group
Applicable Standard: ISO 9001:2015
Certification Registration Number: JP23/00000014
Certification Registration Agency: SGS Japan Co., Ltd. Certification and Business Solution Services
Registration Scope: Provision of Translation Services
International Standard for Translation Services
ISO 17100:2015 Certification
Human Science Co., Ltd. has obtained certification for the international standard for translation services, "ISO 17100:2015 Translation services - Requirements for translation services".
ISO17100:2015 specifies the requirements for key processes and the competence of translators and reviewers for providing high-quality translation services for translation service providers.
We will continue to work together as a staff to manage the quality of translation projects in the future.


Acquisition Date: November 11, 2021
Applicable Standard: ISO 17100:2015
Certification Body: Austrian Standards
Registration Number: S 001248
Certification Scope: Translation Services


Acquisition Date: June 5, 2017
Applicable Standard: ISO 17100:2015
Certification Body: Japan Standards Association Solutions Co., Ltd.
Registration Number: JSAT 029
Certification Scope: Translation services in the fields of medicine and pharmaceuticals, and industry and science and technology (Japanese-English and English-Japanese)
*Not all of our translation services are compliant with "ISO17100".
*If you would like to request ISO17100 compliant translation services, please let us know when placing your order.
Post-edit international standard
ISO 18587:2017 certification
Human Science Co., Ltd. has obtained certification for the international standard for post-editing, "ISO 18587:2017 Translation services - Post-editing of machine translation output".
ISO 18587:2017 specifies requirements for the main processes and competencies of translators and reviewers for providing high-quality post-editing services for translation service providers.
We will continue to work together as a staff to manage the quality of translation projects in the future.